In today’s digital age, websites play a crucial role in businesses and individuals alike. It is where we interact, exchange information, and conduct transactions. However, with the increasing dependence on websites, cyber attacks have become a pressing concern. Hackers are continuously finding new ways to compromise websites, steal data, and disrupt online operations. It is imperative for website owners and users to recognize these attacks and take appropriate measures to safeguard their online presence. In this article, we will dive into the world of cyber attacks on websites and explore ways to protect your website from them.
What is a Cyber Attack?
A Cyber Attacks is a deliberate and malicious attempt by individuals, groups, or organizations to compromise the confidentiality, integrity, or availability of computer systems, networks, or digital data. These attacks are typically executed using a range of techniques and technologies to exploit vulnerabilities or weaknesses in digital systems for various purposes, often with the intent to steal information, disrupt services, or cause harm.
Is Cyber Attacks dangerous?
Cyber Attacks are highly perilous. They can cause significant harm, both in terms of financial losses and damage to an individual or organization’s reputation. These attacks can result in the theft of sensitive data, financial fraud, disruption of essential services, and even the compromise of national security. Cyber Attacks can harm individuals by exposing their personal information or compromising their online privacy. Additionally, they can cripple businesses and government agencies, leading to substantial financial losses and legal repercussions. The evolving nature of cyber threats makes it essential for individuals and organizations to prioritize cybersecurity to mitigate these dangers.

The impact of cyber attacks
The impacts of cyberattacks can be significant and wide-ranging. Here are some of the consequences of cyberattacks in American English:
- Financial Losses
Cyberattacks can result in substantial financial losses for individuals, businesses, and organizations. This includes direct theft of funds, fraudulent transactions, and the cost of restoring systems and data. - Data Breaches
One of the most common consequences is data breaches, where sensitive information such as personal data, financial records, and intellectual property is exposed. This can lead to identity theft, financial fraud, and reputational damage. - Reputational Damage
Cyberattacks can tarnish the reputation of individuals and organizations. Customers and clients may lose trust if their data is compromised, leading to a loss of business and credibility. - Operational Disruption
Cyberattacks can disrupt essential business operations by disabling computer systems, networks, or online services. This downtime can result in lost productivity and revenue. - Legal and Regulatory Consequences
Data breaches and cyberattacks often trigger legal and regulatory obligations. Organizations may face fines, lawsuits, and legal penalties for failing to protect customer data adequately. - Intellectual Property Theft
Cybercriminals may target intellectual property, trade secrets, or proprietary information, which can lead to unfair competition and financial losses. - Ransomware Demands
In the case of ransomware attacks, victims may be forced to pay a ransom to regain access to their data or systems, resulting in financial losses. - National Security Risks
Certain cyberattacks, such as those targeting critical infrastructure or government systems, can pose national security risks. They may compromise essential services and systems. - Loss of Customer Trust
Businesses that suffer cyberattacks risk losing the trust and confidence of their customers, which can be challenging to rebuild. - Cost of Remediation
Recovering from a cyberattack involves costs related to investigating the breach, restoring systems, implementing security measures, and providing identity theft protection to affected parties. - Long-Term Repercussions
Some cyberattacks have long-term consequences, with data breaches or vulnerabilities surfacing months or even years after the initial attack. - Emotional Impact
Individuals who fall victim to cyberattacks may experience stress, anxiety, and emotional distress due to the violation of their privacy and security.
Overall, the impacts of cyberattacks underscore the importance of robust cybersecurity measures and preparedness to mitigate these risks and consequences.
What are the 5 types of cyber attacks?
Cyber attacks on websites have become more prevalent and sophisticated than ever. Hackers target websites for various reasons, including financial gain, political motives, or simply for the thrill of causing chaos. Common types of cyber attacks on websites include:
- Distributed Denial of Service (DDoS) Attacks
In a DDoS attack, hackers overwhelm a website with excessive traffic, rendering it inaccessible to legitimate users. This attack aims to disrupt the website’s service and can result in significant financial losses. - SQL Injection
In an SQL injection attack, hackers manipulate a website’s database by injecting malicious code into input fields. This attack allows them to gain unauthorized access to sensitive information or modify website content. - Cross-Site Scripting (XSS)
An XSS attack occurs when hackers inject malicious scripts into trusted websites. When users visit these websites, the scripts execute on their browsers, allowing hackers to steal user data, plant malware, or redirect users to malicious websites. - Phishing
Phishing attacks are designed to trick users into revealing sensitive information, such as login credentials or credit card details. Hackers often create fake websites that resemble legitimate ones, luring users to enter their personal information unwittingly. - Malware Attacks
Malware attacks involve infecting websites with malicious software. This software can then exploit vulnerabilities on users’ computers, steal data, or gain unauthorized access to their systems.
These are just a few examples of the various cyber attacks that websites face regularly. Knowing and understanding these attacks is the first step in protecting your website and users.
What is common cyber attacks?
Common cyberattacks are malicious activities carried out by cybercriminals with the intent of compromising computer systems, networks, and data. These attacks can cause financial losses, data breaches, and damage to an individual’s or organization’s reputation. Here are some common cyberattacks:
- Phishing
Phishing attacks involve tricking individuals into revealing sensitive information, such as login credentials or financial details, by posing as a trustworthy entity via email, social media, or websites. - Malware
Malware, short for malicious software, includes viruses, Trojans, ransomware, and spyware. These programs are designed to infiltrate and damage computer systems or steal sensitive information. - Ransomware
Ransomware is a type of malware that encrypts a victim’s data and demands a ransom payment in exchange for the decryption key. If the ransom is not paid, the victim’s data may be permanently lost. - Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks
These attacks flood a target system or network with excessive traffic, causing it to become unavailable to users. DDoS attacks involve multiple compromised devices working in unison. - Man-in-the-Middle (MitM) Attacks
In a MitM attack, an attacker intercepts and potentially alters communications between two parties without their knowledge. This allows the attacker to eavesdrop on sensitive information. - SQL Injection
SQL injection attacks target websites and applications by injecting malicious SQL code into input fields. If successful, attackers can gain unauthorized access to a database, potentially compromising user data. - Cross-Site Scripting (XSS)
XSS attacks inject malicious scripts into websites that are then executed by other users’ browsers. This can allow attackers to steal cookies, session tokens, or other sensitive data. - Credential Stuffing
In this attack, cybercriminals use previously stolen login credentials to gain unauthorized access to multiple accounts, as people often reuse passwords across different services. - Zero-Day Exploits
Zero-day vulnerabilities are security flaws that are not yet known to the software vendor. Cyberattackers exploit these vulnerabilities before they can be patched or fixed. - Social Engineering
Social engineering attacks manipulate individuals into divulging confidential information or performing actions that compromise security. This can involve techniques like pretexting, baiting, or tailgating. - Brute Force Attacks
In a brute force attack, attackers attempt to gain access to a system or account by systematically trying every possible password until the correct one is found. - IoT (Internet of Things) Exploitation
As more devices become connected to the internet, attackers may target vulnerable IoT devices to gain unauthorized access to networks or compromise user privacy. - Malvertising
Malvertisements are online ads that contain malicious code. Clicking on these ads can lead to malware infections or other security risks. - Email Spoofing
Attackers use email spoofing to make an email appear as though it comes from a trusted source. This can be used for phishing or other deceptive purposes. - Watering Hole Attacks
In a watering hole attack, attackers compromise a website that is frequently visited by their target audience. When users visit the compromised site, they may unknowingly download malware or become victims of other attacks.
To protect against these common cyberattacks, individuals and organizations should employ robust cybersecurity practices, such as regularly updating software, using strong and unique passwords, educating users about phishing, and implementing network security measures.

3 biggest cyber attacks in the world
In an increasingly interconnected world, cyberattacks have become a pervasive threat, targeting individuals, businesses, and even governments. These attacks can wreak havoc, leading to substantial financial losses, reputational damage, and widespread disruption. Here, we delve into three of the most significant cyberattacks in recent history, each leaving an indelible mark on the global cybersecurity landscape.
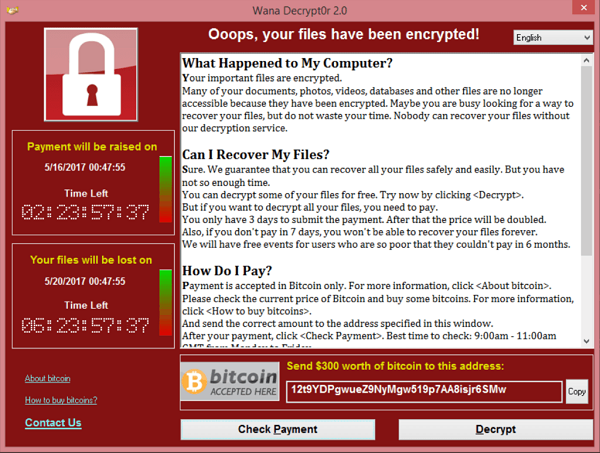
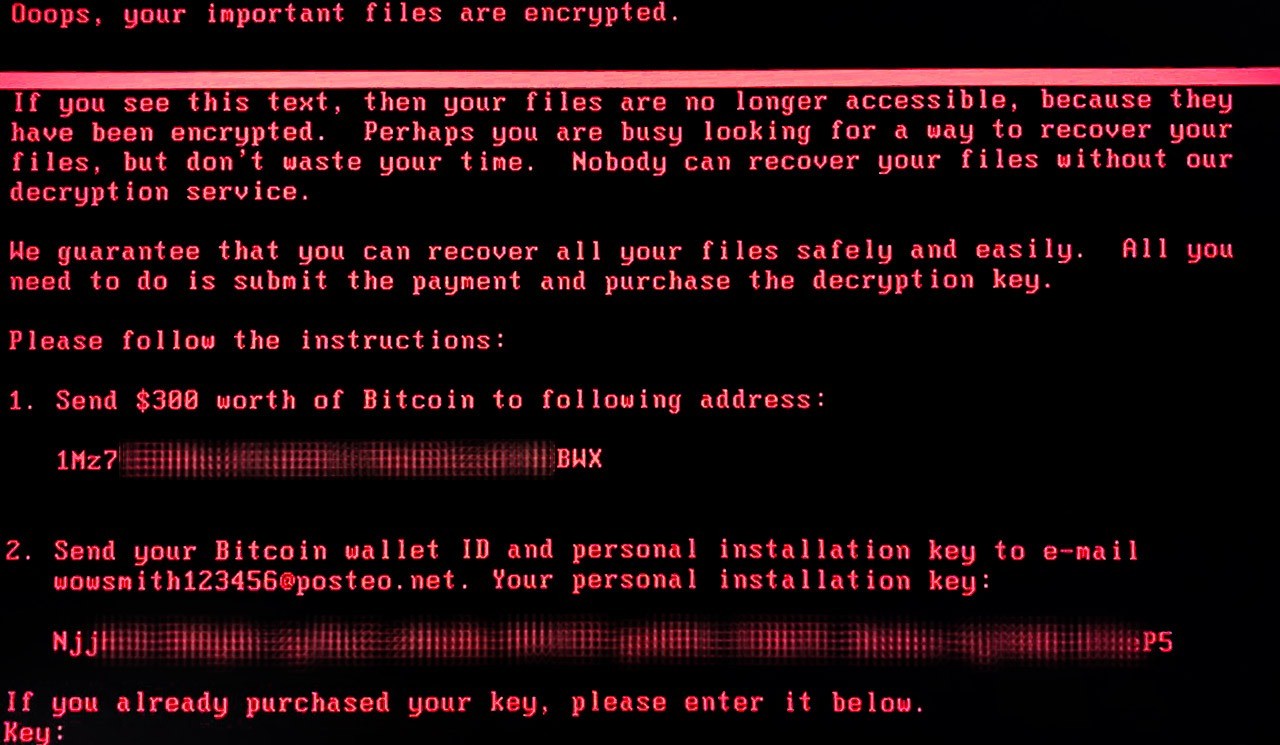
- WannaCry Ransomware Attack (2017):

- Description: The WannaCry ransomware attack of May 2017 stands as one of the most infamous cyberattacks in history. This global assault affected over 150 countries, exploiting a vulnerability in Microsoft Windows operating systems. The malware worked by encrypting data on infected computers and subsequently demanded a ransom payment in Bitcoin in exchange for the decryption key.
- Impact: The attack had far-reaching consequences, disrupting thousands of organizations, including healthcare systems and government agencies. The sheer scale of WannaCry underscored the critical importance of promptly updating and patching software systems to protect against known vulnerabilities. Furthermore, it heightened awareness of the pervasive threat posed by ransomware attacks.
- NotPetya (ExPetr) Ransomware Attack (2017):

- Description: In June 2017, the NotPetya ransomware attack, also known as ExPetr or Petya, sent shockwaves through the global cybersecurity community. Initially targeting Ukraine, this malware rapidly spread worldwide. NotPetya encrypted files on infected systems, demanding a ransom for decryption. However, it is widely believed that the primary objective was to cause widespread damage rather than financial gain.
- Impact: NotPetya disrupted numerous global businesses, resulting in substantial financial losses. The attack served as a stark reminder of the critical need for robust cybersecurity practices and effective patch management. It also prompted discussions about the motivations behind cyberattacks, moving beyond mere financial incentives to include geopolitical and strategic considerations.
- Equifax Data Breach (2017):

- Description: In September 2017, Equifax, one of the largest credit reporting agencies in the United States, fell victim to a devastating data breach. Cybercriminals exploited a vulnerability in the company’s web application software, leading to the exposure of sensitive personal information belonging to approximately 147 million individuals.
- Impact: The Equifax breach had far-reaching consequences, with victims facing risks of identity theft, financial fraud, and other malicious activities. The incident triggered legal and regulatory scrutiny, shedding light on the need for stringent data protection measures and sparking debates about data privacy and cybersecurity regulations.
These cyberattacks serve as stark reminders of the ever-present threat of cybercrime and the need for continuous vigilance and cybersecurity measures to protect individuals and organizations from such large-scale attacks.
How to Protect Your Website?
Fortunately, there are steps you can take to protect your website and mitigate the risk of cyber attacks. Consider implementing the following measures:
- Keep Software Updated
Regularly update your website’s software, including content management systems (CMS), plugins, and themes. Updates often address security vulnerabilities, protecting your website from potential attacks. - Use Strong and Unique Passwords
Ensure that all user accounts on your website have strong and unique passwords. Encourage users to choose passwords that include a combination of letters, numbers, and special characters to reduce the risk of brute-force attacks. - Employ Secure Socket Layer (SSL) Certificates
SSL certificates encrypt communication between your website and users’ browsers, ensuring data privacy and preventing attacks like eavesdropping or data interception. - Regularly Backup Your Website
Regularly backup your website’s files and databases. In the event of a cyber attack, you can restore your website to its previous state without compromising data or functionality. - Implement Web Application Firewalls (WAF)
A WAF acts as a shield between your website and potential attackers. It monitors incoming traffic and blocks suspicious or malicious requests, preventing attacks like SQL injection and XSS. - Educate Your Users
Train your website’s users to recognize and avoid common cyber threats, such as phishing emails or suspicious links. By educating them, you create an extra layer of defense against potential attacks. - Monitor Website Traffic
Regularly monitor your website’s traffic and look for unusual patterns or suspicious activities. This helps you detect potential attacks early and take immediate action. - Conduct Regular Penetration Testing
Hire professionals to conduct penetration tests on your website. These tests simulate real-world attacks to identify vulnerabilities and provide recommendations for improving your website’s security. - Limit User Privileges
Grant users the minimum privileges necessary to perform their tasks. By limiting user privileges, you reduce the risk of unauthorized access or accidental insider threats. - Stay Informed
Keep up to date with the latest trends and news in cybersecurity. Understanding the evolving landscape of cyber attacks allows you to adapt your website’s security measures accordingly.
Best providers of cybersecurity services (Protection From Cyber Attacks)
In our increasingly digital world, the threat of cyberattacks looms large for individuals, businesses, and governments alike. To fortify defenses against these evolving threats, many turn to cybersecurity service (Protection From Cyber Attacks) providers that offer specialized expertise and comprehensive protection.
- Symantec Corporation (Now Broadcom)
- Description: Symantec, now a part of Broadcom, stands as a global heavyweight in the realm of cybersecurity (Protection From Cyber Attacks) solutions. With a rich legacy and an expansive portfolio of services, Symantec caters to a diverse clientele, safeguarding them against a multitude of cyber threats. Their offerings span endpoint protection, threat intelligence, cloud security, and network security.
- Notable Features: Symantec’s arsenal includes advanced threat detection and response capabilities, bolstered by machine learning-powered security measures. Furthermore, their Global Intelligence Network ensures that clients stay ahead of emerging threats, making Symantec a stalwart guardian against cyber adversaries.
- McAfee
- Description: McAfee, a venerable name in the cybersecurity landscape, delivers a wide spectrum of solutions tailored for individuals, businesses, and governmental entities. Their offerings encompass antivirus software, endpoint protection, network security, and cloud security services. McAfee is synonymous with proactive cybersecurity measures that have kept users safe for decades.
- Notable Features: McAfee’s suite of solutions incorporates threat intelligence, behavioral analytics, and robust cloud-based security. These elements collectively create a formidable defense against an array of cyber threats, ensuring that users can navigate the digital realm with confidence.
- FireEye, Inc.
- Description: FireEye, Inc. distinguishes itself as a cybersecurity company with a specialization in advanced threat intelligence and protection. Their suite of services includes threat detection, incident response, and email security (Protection From Cyber Attacks). FireEye is renowned for its ability to identify and mitigate sophisticated, targeted cyber threats that may elude conventional security measures.
- Notable Features: FireEye’s strength lies in its real-time threat intelligence platform, which offers unparalleled insights into emerging threats. This empowers organizations to respond promptly and effectively when confronted with cyberattacks, enhancing their overall cybersecurity posture.
- Palo Alto Networks
- Description: Palo Alto Networks is a leading provider of next-generation cybersecurity solutions. Their portfolio encompasses firewall protection, cloud security, and advanced threat prevention services. They are known for their innovative approach to cybersecurity.
- Notable Features: Palo Alto Networks offers advanced firewalls with granular control over applications and threats. Their cloud security solutions provide protection for modern cloud environments, making them well-suited for businesses embracing cloud technologies.
- Trend Micro
- Description: Trend Micro is a global cybersecurity company offering a range of services, including endpoint security, network defense, and cloud security. They focus on protecting against evolving cyber threats with advanced solutions.
- Notable Features: Trend Micro’s services include advanced threat detection and response capabilities, as well as cloud security solutions designed to safeguard data and applications in the cloud. Their solutions cater to businesses of all sizes.
- Check Point Software Technologies
- Description: Check Point Software Technologies is a cybersecurity company that provides comprehensive threat prevention solutions. Their offerings include firewall protection, threat intelligence, and mobile security solutions.
- Notable Features: Check Point’s threat prevention solutions are designed to proactively identify and block cyber threats across various attack vectors. They offer real-time threat intelligence to keep organizations updated on emerging threats.
These cybersecurity service (Protection From Cyber Attacks) providers are renowned for their commitment to protecting individuals and organizations against cyber threats. Their offerings encompass a broad spectrum of security measures, from traditional antivirus solutions to advanced threat intelligence and incident response capabilities, ensuring comprehensive protection in an ever-evolving threat landscape.
Conclusion
Cyber attacks on websites are a real and growing threat in today’s digital world. By recognizing common attack types and implementing proactive security measures, you can protect your website and users from potential harm. Emphasize the importance of cybersecurity (Protection From Cyber Attacks) to your team and users and stay vigilant in safeguarding your online presence. Remember, prevention and preparedness are key to countering cyber attacks!