In today’s digital age, where cyber threats are becoming increasingly sophisticated, protecting your network is more important than ever. A firewall network is one of the most critical tools in the cybersecurity arsenal, acting as a barrier between your internal network and the outside world. Whether you’re a business owner, an IT professional, or just someone curious about how to keep your data safe, understanding firewalls is essential. This article will dive deep into a firewall network, how it works, and why it’s a cornerstone of modern cybersecurity.
What is a Firewall Network?
A firewall network is a security system designed to monitor and control incoming and outgoing traffic based on predetermined security rules. Think of it as a digital gatekeeper that decides who gets in and who stays out. Firewalls can be hardware-based, software-based, or a combination of both, and they protect networks from unauthorized access, malware, and other cyber threats.
Firewalls operate by establishing a barrier between a trusted internal network and untrusted external networks, such as the Internet. They analyze data packets—small chunks of data transmitted over a network—and determine whether they should be allowed through based on the rules set by the network administrator. This process ensures that only safe and authorized traffic can enter or leave the network.
How Does a Firewall Work?
To understand how a firewall works, imagine it as a security guard at the entrance of a building. The guard checks everyone’s ID and only allows entry to those who meet specific criteria. Similarly, a firewall examines data packets and uses a set of rules to decide whether to allow or block them. These rules can be based on various factors, such as the source or destination IP address, the data transmitted type, and the port being used.
For example, if a firewall is configured to block traffic from a specific IP address, any data packets from that address will be denied entry. Likewise, if the firewall is set to allow only HTTP traffic (used for web browsing), any other type of traffic, such as FTP (used for file transfers), will be blocked.
Types of Firewalls
There are different types of firewalls, each with its own strengths and weaknesses. Understanding these types can help you choose the right one for your needs.
- Packet-filtering firewalls are the most basic type of firewalls. They examine each data packet and compare it against a set of rules. If the packet meets the criteria, it’s allowed through; if not, it’s blocked. While simple and efficient, packet-filtering firewalls lack advanced features like deep packet inspection.
- Stateful Inspection Firewalls: These firewalls go a step further by keeping track of the state of active connections. They examine individual packets and consider the context of the traffic, making them more effective at detecting and blocking suspicious activity.
- Proxy Firewalls: Acting as an intermediary between users and the Internet, proxy firewalls receive and forward requests on behalf of the user. This adds an extra layer of security by hiding the user’s IP address and filtering traffic at the application level.
- Next-Generation Firewalls (NGFW): These advanced firewalls combine traditional firewall features with additional capabilities like intrusion prevention, deep packet inspection, and application awareness. NGFWs are designed to protect against modern threats like advanced malware and zero-day attacks.
- Unified Threat Management (UTM) Firewalls: UTMs are all-in-one security devices that integrate multiple features, including firewalls, antivirus, and content filtering. They are ideal for small to medium-sized businesses looking for comprehensive protection.

Why Are Firewalls Important?
Firewalls are crucial in protecting networks from a wide range of cyber threats. Without a firewall, your network is like an open door, inviting hackers, malware, and other malicious actors to wreak havoc. Here are some key reasons why firewalls are essential:
- Prevent Unauthorized Access: Firewalls block unauthorized users from accessing your network, ensuring that only legitimate traffic is allowed.
- Stop Malware and Viruses: Firewalls help prevent malware and viruses from infecting systems by filtering out malicious traffic.
- Protect Sensitive Data: Firewalls safeguard sensitive information, such as customer data and intellectual property, from theft or compromise.
- Enhance Network Performance: By blocking unnecessary traffic, firewalls can improve network performance and reduce bandwidth usage.
- Comply with Regulations: Many industries have strict cybersecurity regulations that require firewalls to protect sensitive data.
Firewall Configuration Best Practices
Configuring a firewall properly is just as important as having one. A poorly configured firewall can leave your network vulnerable to attacks. Here are some best practices to follow:
- Default Deny Rule: Start with a default deny rule, which blocks all traffic. Then, create specific rules to allow only the traffic you need.
- Regular Updates: Keep your firewall’s firmware and software updated to protect against the latest threats.
- Least Privilege Principle: Only grant the minimum level of access necessary for users and applications to function.
- Monitor and Log Traffic: Regularly review firewall logs to detect and respond to suspicious activity.
- Segment Your Network: Divide your network into smaller segments and use firewalls to control traffic between them. This limits the spread of attacks.
Common Firewall Challenges
While firewalls are powerful tools, they are not without their challenges. Some common issues include:
- False Positives: Firewalls may sometimes block legitimate traffic, causing disruptions.
- Complexity: Managing and configuring firewalls can be complex, especially for large networks.
- Performance Impact: Firewalls can slow down network performance, particularly if not properly optimized.
- Evolving Threats: Cyber threats constantly change, and firewalls must be updated regularly.
Firewall vs. Other Security Tools
Firewalls are just one piece of the cybersecurity puzzle. They work best when used in conjunction with other security tools, such as:
- Antivirus Software: Protects against malware and viruses.
- Intrusion Detection Systems (IDS): Monitors network traffic for suspicious activity.
- Virtual Private Networks (VPNs): Encrypts data transmitted over the Internet.
- Endpoint Security: Protects individual devices, such as laptops and smartphones.
A Modern Approach to Network Security
In the ever-evolving cybersecurity landscape, the “Nest 3 Firewall Service” concept represents a cutting-edge approach to protecting networks. This advanced service combines three layers of firewall protection—hardware, software, and cloud-based—to create a robust defense system. Integrating these layers ensures comprehensive coverage against various cyber threats. Let’s break down what each layer entails and how they work together to provide unparalleled security.
Hardware Firewall
The first layer of the Nest 3 Firewall Service is the hardware firewall. This physical device sits between your internal network and the outside world, acting as the first line of defense. Hardware firewalls are typically installed at the network perimeter, monitoring and filtering incoming and outgoing traffic.
Key Features of Hardware Firewalls:
- High Performance: Hardware firewalls are designed to handle large traffic volumes without slowing your network.
- Dedicated Security: Since they are standalone devices, hardware firewalls focus solely on protecting your network, reducing the risk of conflicts with other software.
- Scalability: Hardware firewalls can be easily upgraded or replaced to meet the growing needs of your network.
Why It Matters: A hardware firewall provides a strong foundation for your network security, blocking unauthorized access and filtering out malicious traffic before it reaches your internal systems.
Software Firewall
The second layer of the Nest 3 Firewall Service is the software firewall. Unlike hardware firewalls, software firewalls are installed on individual devices, such as computers, servers, or mobile devices. They provide an additional layer of protection by monitoring and controlling traffic at the device level.
Key Features of Software Firewalls:
- Granular Control: Software firewalls allow you to set specific rules for each device, giving you more control over what traffic is allowed.
- Application-Level Filtering: They can filter traffic based on the application, ensuring that only trusted programs can access the network.
- User-Specific Rules: Software firewalls can be configured to apply different rules for different users, enhancing security for sensitive accounts.
Why It Matters: A software firewall adds an extra layer of security by protecting individual devices from threats that may bypass the hardware firewall. This is especially important for remote workers or devices that connect to public networks.
Cloud-Based Firewall
The third layer of the Nest 3 Firewall Service is the cloud-based firewall. As more businesses move to the cloud, traditional firewalls are insufficient. Cloud-based firewalls protect cloud environments, ensuring your data and applications are secure, no matter where they are hosted.
Key Features of Cloud-Based Firewalls:
- Flexibility: Cloud-based firewalls can be easily scaled up or down to match your needs, making them ideal for businesses with fluctuating traffic.
- Centralized Management: They allow you to manage firewall rules and policies from a single console, simplifying administration.
- Real-Time Updates: Cloud-based firewalls are continuously updated to protect against the latest threats, ensuring your network is always secure.
Why It Matters: A cloud-based firewall protects cloud-based applications and data. It ensures that your network security extends beyond your physical premises, covering all aspects of your digital infrastructure.
How the Nest 3 Firewall Service Works Together
The true power of the Nest 3 Firewall Service lies in the seamless integration of its three layers. Here’s how they work together to provide comprehensive protection:
- Traffic Filtering: The hardware firewall filters traffic at the network perimeter, blocking unauthorized access and malicious traffic.
- Device-Level Protection: The software firewall adds an extra layer of security by protecting individual devices from threats that may bypass the hardware firewall.
- Cloud Security: The cloud-based firewall ensures your cloud environments are secure, providing real-time updates and centralized management.
By combining these layers, the Nest 3 Firewall Service creates a multi-layered defense system that effectively prevents cyberattacks. Whether you’re dealing with malware, phishing attempts, or advanced persistent threats, this service ensures your network is protected at every level.
Future of Firewall Networks
As cyber threats continue to evolve, so too will firewall technology. Some emerging trends include:
- AI and Machine Learning: Firewalls will increasingly use AI to detect and respond to threats in real time.
- Cloud-Based Firewalls: With the rise of cloud computing, firewalls are being adapted to protect cloud environments.
- Zero Trust Architecture: This approach assumes that no user or device can be trusted by default, requiring continuous verification.
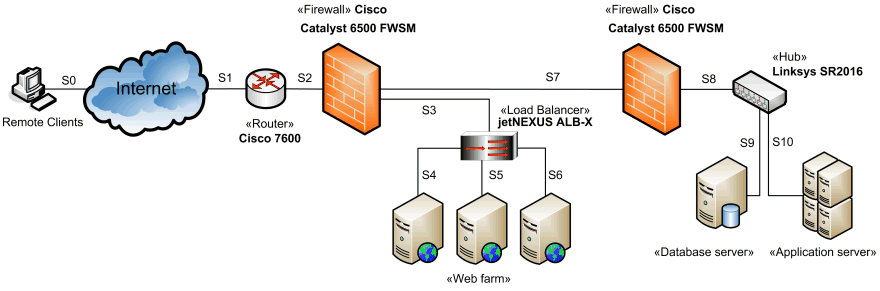
Top Choices for Robust Network Security
Choosing the right firewall provider is crucial for ensuring the safety and integrity of your network. With so many options available, it can be challenging to determine which provider offers the best combination of features, performance, and reliability. In this section, we’ll explore the top three firewall providers in the industry, highlighting their strengths and what makes them stand out. Whether you are a small business owner or an IT professional managing a large enterprise, these providers offer solutions tailored to your needs.
Cisco: The Industry Leader in Network Security
For good reason, Cisco is a household name in networking and cybersecurity. As one of the pioneers in firewall technology, Cisco offers a wide range of firewall solutions designed to meet the needs of businesses of all sizes. Their firewalls are known for their reliability, advanced features, and seamless integration with other Cisco products.
Key Features of Cisco Firewalls:
- Advanced Threat Protection: Cisco firewalls come equipped with features like intrusion prevention, malware blocking, and URL filtering to protect against a wide range of threats.
- Scalability: Whether a small business or a large enterprise, Cisco offers firewalls that can scale with your needs.
- Unified Management: Cisco’s Security Manager allows you to manage all your firewall policies from a single console, simplifying administration.
- Integration with Cisco Ecosystem: If you’re already using other Cisco products, their firewalls integrate seamlessly, providing a cohesive security solution.
Why Choose Cisco?
Cisco is ideal for businesses that need a reliable, feature-rich firewall solution. Their reputation for quality and innovation makes them a top choice for organizations looking to future-proof their network security.
Palo Alto Networks: The Innovator in Next-Generation Firewalls
Palo Alto Networks is widely regarded as a leader in next-generation firewalls (NGFWs). Their firewalls are designed to provide advanced protection against modern threats, making them a favorite among enterprises and organizations with complex security needs.
Key Features of Palo Alto Networks Firewalls:
- Application-Based Filtering: Palo Alto firewalls can identify and control traffic based on the application, giving you granular control over what’s allowed on your network.
- Threat Prevention: Their firewalls include advanced threat prevention features like sandboxing, which isolates and analyzes suspicious files to detect zero-day threats.
- Cloud-Based Management: Palo Alto’s Panorama platform allows you to manage multiple firewalls from a single cloud-based console, making enforcing consistent security policies across your organization easy.
- AI and Machine Learning: Palo Alto integrates AI and machine learning into its firewalls to detect and respond to threats in real-time.
Why Choose Palo Alto Networks?
Palo Alto Networks is an excellent choice if you’re looking for cutting-edge technology and advanced threat protection. Their focus on innovation and ability to handle complex security challenges make them a top contender in the firewall market.
Fortinet: The All-in-One Security Solution
Fortinet is another heavyweight in the firewall industry, known for its comprehensive security solutions and high-performance firewalls. Their FortiGate firewalls are particularly popular for delivering robust security without compromising on performance.
Key Features of Fortinet Firewalls:
- Unified Threat Management (UTM): Fortinet’s firewalls combine multiple security features, including antivirus, intrusion prevention, and web filtering, into a single device.
- High Performance: Fortinet firewalls are designed to handle high traffic volumes without slowing down your network, making them ideal for businesses with demanding workloads.
- Flexible Deployment: Whether you need an on-premises firewall, a cloud-based solution, or a hybrid approach, Fortinet offers flexible deployment options to suit your needs.
- Security Fabric: Fortinet’s Security Fabric integrates all its security products, providing a unified and coordinated defense against threats.
Why Choose Fortinet?
Fortinet is an excellent choice for businesses that want an all-in-one security solution. Their firewalls are powerful, versatile, and easy to manage, making them a favorite among IT professionals.
Comparing the Top 3 Firewall Providers
To help you decide which provider is right for you, here’s a quick comparison of the key features offered by Cisco, Palo Alto Networks, and Fortinet:
| Feature | Cloudflare | Sophos | Zscaler |
|---|---|---|---|
| Cloud-Based | Yes | No (Hybrid Option Available) | Yes |
| Managed Service | No | Yes | No |
| DDoS Protection | Yes | Limited | Yes |
| Zero Trust Security | Limited | No | Yes |
| Global Coverage | Yes | Limited | Yes |
| Advanced Threat Protection | Yes | Yes | Yes |
Which Firewall Network Provider is Right for You?
The best firewall provider for your organization depends on your specific needs and priorities. Here’s a quick guide to help you decide:
- Choose Cisco if you value reliability, seamless integration with other Cisco products, and a proven track record in the industry.
- Choose Palo Alto Networks if you need advanced threat protection, application-based filtering, and cutting-edge technology.
- Choose Fortinet if you’re looking for an all-in-one solution that combines high performance with comprehensive security features.
Choosing the Right Firewall for Your Needs
Selecting the proper firewall depends on your specific requirements. Consider factors like the size of your network, the types of threats you face, and your budget. A UTM firewall may be sufficient for small businesses, while larger enterprises may need an NGFW.
Conclusion
A firewall network is indispensable for protecting digital assets in an increasingly connected world. Understanding how firewalls work, the different types available, and best practices for configuration can significantly enhance your network’s security. As cyber threats continue to grow, staying informed and proactive is the best way to keep your data safe. Remember, a strong firewall is your first line of defense against cybercrime.