Email scams aren’t just annoying—they’re dangerous. One click on the wrong link or sharing your personal info with the bad ‘support team’ can lead to identity theft, financial loss, or even a full-on data breach. Whether you’re checking emails for work or casually scrolling through promotions and newsletters, cybercriminals are banking on the fact that you’re busy, distracted, or unfamiliar with their sneaky tactics. These tactics include creating legitimate fake websites, using urgent language to pressure you into immediate action, or impersonating Someone you know to gain your trust.
This guide simplifies everything you need to know about avoiding email scams—from identifying red flags to adopting smarter habits that secure your digital life. We’ll keep things straightforward, free of jargon, and easily digestible. When it comes to online safety, everyone should feel empowered to grasp the risks and protect themselves.
Let’s delve into the essential knowledge you need to outsmart scammers before they can outsmart you. This guide is your proactive tool to take control of your online safety.
Understanding What Email Scams Really Are
Let’s start with the basics: what exactly is an email scam?
An email scam is any deceptive email intended to trick the recipient into revealing sensitive information, clicking on a malicious link, or making a payment. These scams are designed to look convincing—often posing as banks, tech companies, delivery services, or even friends and coworkers.
There are many types of email scams:
- Phishing Emails: These attempt to “fish” for your information by pretending to be from a trusted source.
- Business Email Compromise (BEC): Scammers impersonate executives or colleagues to manipulate staff into transferring money or data.
- Advance Fee Fraud: Promises of lottery winnings or investment opportunities if you pay an upfront fee.
- Tech Support Scams: You get an email claiming a virus on your computer, and a “technician” offers to fix it—usually for a price or remote access.
The goal? Get your money, steal your identity, or gain unauthorized access to sensitive systems.
The Psychology Behind Email Scams
Email scams aren’t just technical—they’re psychological. Scammers use emotional manipulation to bypass your logic and get you to act fast.
They rely on:
- Fear: “Your account has been hacked!”
- Greed: “Claim your $100 gift card!”
- Curiosity: “Someone has a secret crush on you. Click here to find out who.”
- Obedience: “This is your manager—send me the payroll list ASAP.”
Understanding that these tactics are intentional and calculated helps you step back and evaluate an email calmly before reacting.
Guide to Avoiding Email Scams: Stay Safe in Your Inbox
Recognizing the Red Flags
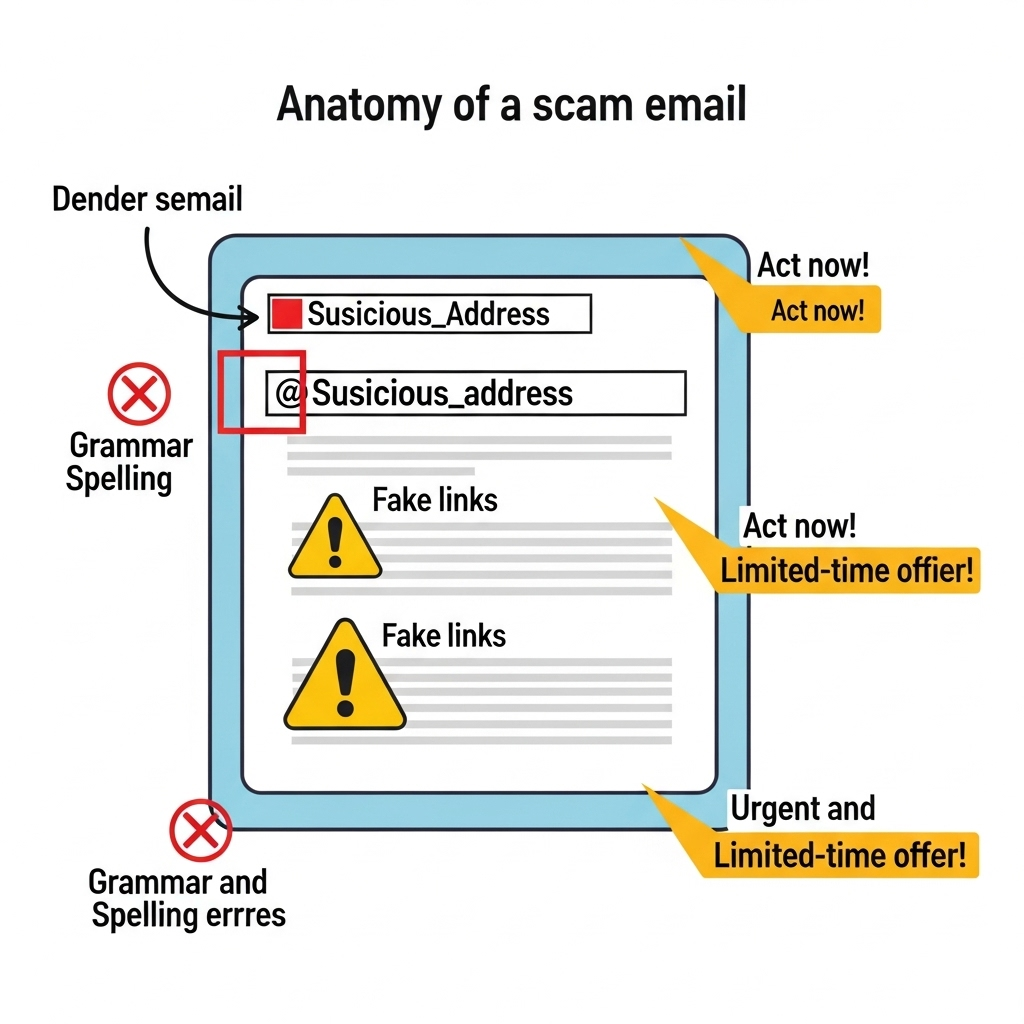
Spotting an email scam starts with paying attention to the little details. Scammers are crafty, but they often leave behind subtle clues that reveal their intentions.
Common red flags include:
- Urgent or threatening language, such as “Your account will be suspended!” or “Immediate action required!” are classic pressure tactics.
- Unusual sender address: The name might say “Amazon Support,” but the email comes from support@amaz0n-updates.ru.
- Grammar and spelling mistakes: Legitimate companies proofread their messages. Sloppy writing is a giveaway.
- Suspicious links or attachments: Hover over any link before clicking. If it doesn’t match the company’s official domain, avoid it.
- Unusual requests: No honest company will ask for your password, Social Security number, or payment info over email.
Learning to recognize these signs is your first defense against falling for a scam.

Why Phishing Is So Dangerous
Phishing is the most common and most effective email scam tactic today. It’s also constantly evolving.
A phishing email usually impersonates a trusted company or individual and includes a fake link or attachment. Once clicked, you might be redirected to a bogus login page, unknowingly downloading malware or giving away your credentials.
Variants include:
- Spear Phishing: Personalized to the recipient, making it far more believable.
- Whaling: Targeting high-profile individuals like executives.
- Clone Phishing: Copying a legitimate email and replacing a link or file with something malicious.
Because phishing can trick even savvy users, the best protection is staying alert and verifying the sender independently when in doubt.
What to Do If You Receive a Suspicious Email
Even if you’re careful, scams can sneak into your inbox. The key is not to panic—and not to engage.
Here’s what to do:
- Don’t click anything. No links, no attachments. Don’t even reply.
- Could you report it? Most email providers have a “Report phishing” option.
- Block the sender. This helps train your spam filter.
- Check your accounts. If you did click, immediately change your passwords and enable two-factor authentication.
- Scan your device. Use a trusted antivirus tool to look for malware or suspicious activity.
Taking these steps quickly can help reduce or prevent any damage.
Building Better Email Habits
Avoiding scams isn’t just about recognizing them—it’s also about practicing safe habits consistently.
Developing these habits helps:
- Use a strong, unique password for your email account. A password manager can make this easy.
- Enable two-factor authentication (2FA) to add an extra layer of protection.
- Keep software updated, including your browser, operating system, and antivirus.
- Regularly review your inbox and trash for anything odd that might indicate compromise.
- Don’t use public Wi-Fi to check sensitive emails unless you’re on a VPN.
Treat your inbox like your front door. Lock it, monitor it, and never open it for strangers.
Guide to Avoiding Email Scams: Stay Safe in Your Inbox
Top-Tier Email Providers for Security Against Scams
Sometimes, the best way to deal with email scams is to let your provider handle them before they ever reach your inbox. Not all email services are created equal when filtering out phishing attempts, spam, and malicious content. If you’re serious about protecting yourself, choosing an email provider with strong built-in security features is smart.
Here are some of the best email providers known for their top-notch security:
1. ProtonMail
Based in Switzerland and built around privacy, ProtonMail offers end-to-end encryption, zero-access architecture (even if they can’t read your emails), and strong spam/phishing filters. It’s ideal for users who value security and confidentiality.
2. Gmail (Google Workspace)
Google uses machine learning and AI to block over 99.9% of spam, phishing, and malware. With additional security features like two-step verification, Safe Browsing warnings, and SPF/DKIM/DMARC enforcement, Gmail remains a solid choice for personal and business use.
3. Outlook (Microsoft 365)
Outlook, especially with a Microsoft 365 subscription, provides enterprise-level threat detection, attachment scanning, and phishing protection. Microsoft Defender integration helps catch malicious content early, and its link-checking feature enables you to avoid dangerous redirects.
4. Zoho Mail
Zoho offers ad-free email with a strong emphasis on security, including spam filtering, data encryption, and domain-level protection. It’s perfect for businesses looking for a secure, privacy-conscious alternative.
5. Tutanota
Another privacy-focused provider, Tutanota, encrypts everything from subject lines to address books. Its automatic spam filtering and phishing detection are exceptionally reliable, and the service is open-source—excellent for transparency.
Each provider brings a unique mix of features, but they all excel in blocking scams before they land in your inbox. Choosing one of these services adds an extra layer of defense—without requiring you to become a cybersecurity expert.
If you’re still using an outdated or insecure email platform, switching to a modern, security-first provider might be the easiest win for your digital safety.
How to Protect Your Business from Email Fraud
Email scams aren’t just a personal problem but a serious business risk.
Small businesses are especially vulnerable because they often lack dedicated cybersecurity teams. Here’s what helps:
- Staff training: Educate your team to identify phishing attempts and social engineering tactics.
- Internal policies: Never allow sensitive info to be sent over email without verification.
- Use email filters: Advanced spam filters and threat detection tools reduce exposure.
- Monitor unusual activity: Unexpected logins, large attachments, or weird requests should raise red flags.
Creating a culture of awareness is one of the best defenses a company can build.
When Email Scams Get Personal
Scammers are getting more personal than ever. They might research you on social media, spoof people you know, or use details from a previous data breach to make their emails seem more convincing.
This technique, called social engineering, is hazardous because it builds trust. You’re far more likely to comply if you think a scammer is your boss, bank, or family member.
Stay skeptical—even when something seems familiar. If something feels off, verify it through another method before you take action.
Tools That Help You Stay Safe
You don’t have to fight scams alone. Tools are built to keep your email safe and help you spot red flags early.
Some helpful ones include:
- Spam filters: Most email platforms like Gmail or Outlook have robust filters to sort scam emails automatically.
- Browser extensions: Tools like Bitdefender TrafficLight or Norton Safe Web warn you before visiting dangerous sites.
- Email verification tools: Some businesses use services like SPF, DKIM, and DMARC to ensure emails come from trusted sources. Look for authentication icons in your inbox.
- Password managers help prevent password reuse and automatically fill in login details only on correct websites.
Using a combination of these boosts your protection significantly.
Staying Updated on Scam Trends
Scammers are constantly evolving. So should your knowledge.
Subscribe to cybersecurity newsletters, follow tech blogs, and check official resources like:
- The Federal Trade Commission (FTC) – Offers alerts and scam tips.
- Have I Been Pwned – Let you check if your email has been in a data breach.
- StaySafeOnline.org – Offers security tips for individuals and businesses.
Being informed is your best long-term defense. Understanding the threats makes you more prepared to handle them confidently.
Conclusion: Stay Smart, Stay Safe
Email scams aren’t going anywhere, but you can avoid falling into their traps with the proper knowledge and habits. It’s all about being cautious, informed, and proactive. Think before you click, question anything that seems off, and use the tools available to keep your inbox secure.
Digital safety doesn’t have to be complicated—and a few smart changes can go a long way in protecting your personal information, money, and peace of mind. So next time you get that too-good-to-be-true offer or that urgent “account alert,” you’ll know exactly what to do.
Stay alert, stay skeptical, and stay one step ahead.













